Netkiller ISMS 4.2.5 Update Notes
Version: Netkiller ISMS 4.2.5 Update Date: October 27, 2025
Netkiller ISMS 4.2.5 Update Summary
Netkiller ISMS version 4.2.5 is a major update focused on enhancing user experience and strengthening system stability. This release delivers a higher level of information security environment through (1) establishing a more robust security and stability foundation, (2) improving large-scale task processing capabilities and adding key new features, and (3) incorporating user feedback for more intuitive UI/UX improvements.
Above all, we have prioritized reinforcing the system’s security and stability. We’ve comprehensively upgraded the logging library to meet the latest security standards, strengthened database communication security, and made the permission management system more robust. Furthermore, by proactively responding to cloud environment changes, we have secured long-term service stability. Through this, users can utilize the service with greater peace of mind.
The processing capacity and success rate for large-scale external sharing requests have been significantly improved. Requests involving numerous files or recipients are now processed quickly and reliably, enhancing work efficiency. Practical new features have been added to increase management convenience, such as the ability to immediately stop approved shares and set custom times for organization/user synchronization, enabling more flexible and powerful management.
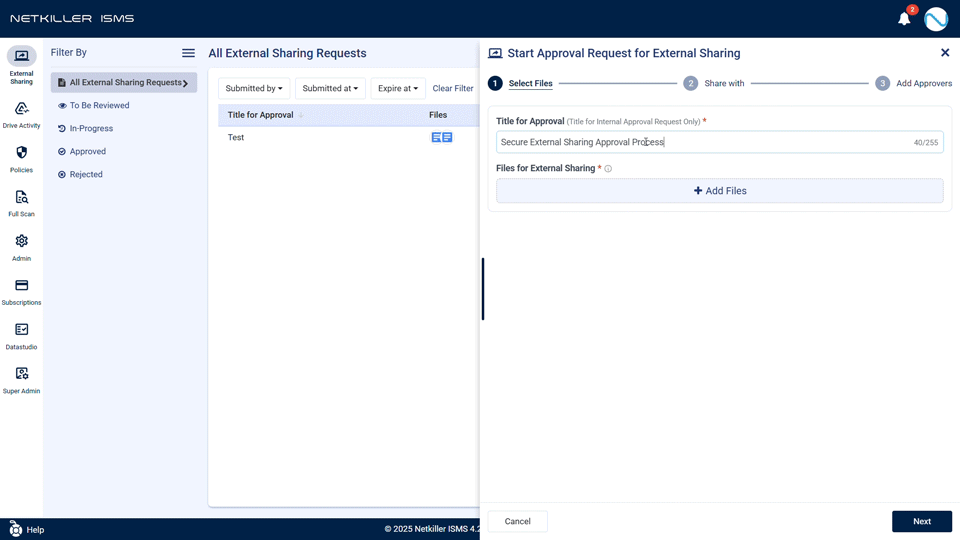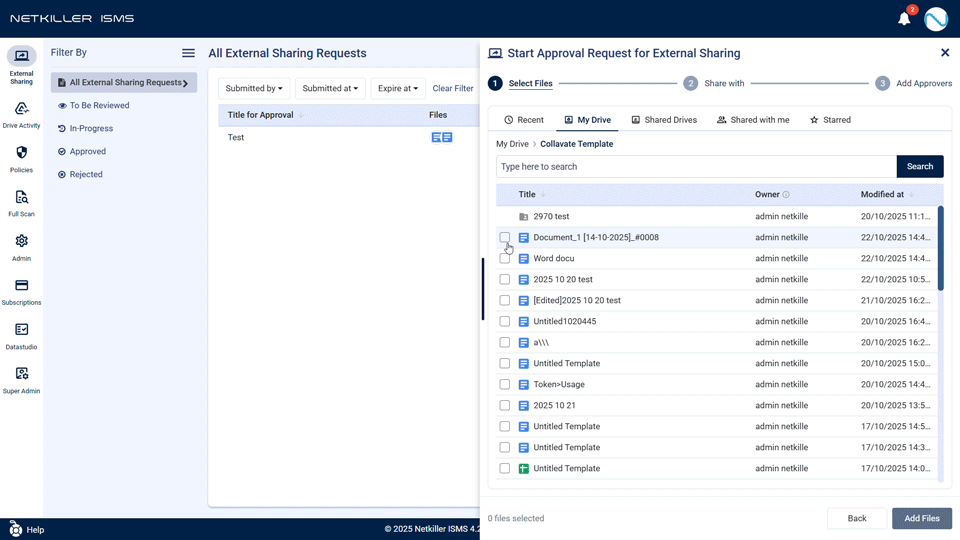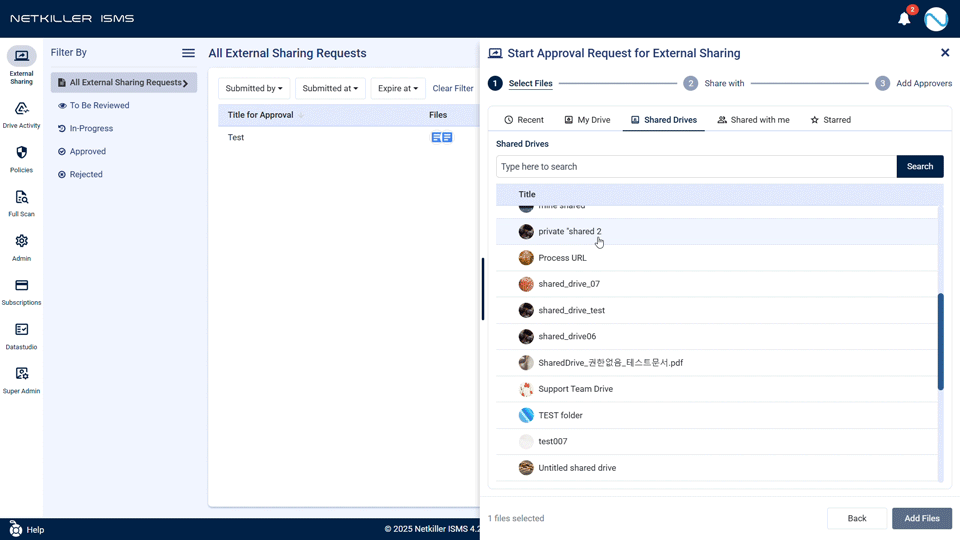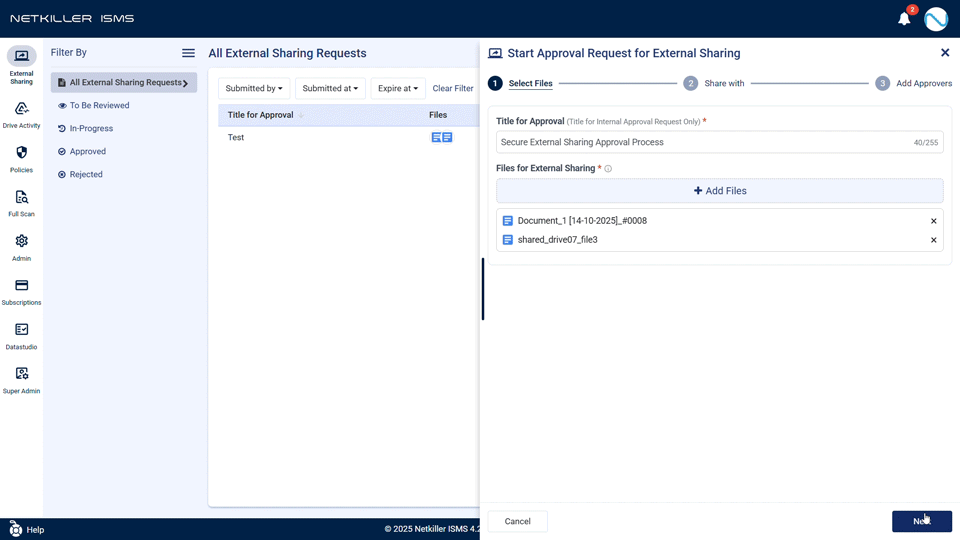
In terms of the User Interface (UI), the file selection method for external sharing has been completely revamped into a Google Drive-like explorer format, making it much easier to find files. The panel resizing function for viewing long filenames has become more convenient, and various improvements reflecting user feedback, such as real-time character count for message input and clearer ‘Full Scan’ progress indication, provide a more intuitive and efficient user experience.
In addition, various improvements have been made throughout the system to enhance stability and data accuracy. With this update, Netkiller ISMS will deliver a safer, faster, and more convenient information security experience.
Netkiller ISMS version 4.2.5 is particularly effective for organizations with the following requirements:
- Organizations seeking to enhance service reliability by applying the latest security technologies.
- Organizations that frequently perform large-scale external sharing with numerous files or users and require stable processing performance.
- Organizations desiring enhanced control functions after external sharing approval (e.g., immediate share termination).
- Organizations wishing to flexibly manage user information synchronization timing according to workflows.
- Organizations looking to check policy violation status through integrated reports and improve management efficiency (New Report Feature).
- Organizations aiming to enhance information security work productivity through a more intuitive and convenient interface.
✨ Enhanced Features and Performance
This update strengthens core system functions and optimizes performance to provide a more stable information security environment, even in large-scale settings.
- Significant Reinforcement of System Security and Stability:
- To comply with the latest security standards and enhance security, the core logging system has been safely upgraded, protecting the system from potential security threats.
- Security for the data transmission process has been strengthened by allowing communication with the database only when encrypted (SSL).
- Access control for administrator functions has been reinforced, enhancing permission system security by ensuring only authorized administrators can use related functions.
- The risk of information exposure has been reduced by ensuring sensitive information (e.g., resident registration numbers) potentially included in policy violation notification emails is securely masked.
- System execution methods have been proactively updated in preparation for future cloud environment changes, ensuring stable, uninterrupted service.
- Innovation in Large-Scale External Sharing Processing Capacity:
- Large-scale external sharing requests involving many files and recipients are now processed quickly and reliably. Processing performance for large requests has been significantly increased, boosting user work efficiency.
- Data consistency is ensured by improving the related logic so that file ownership transfer and inheritance of existing sharing permissions occur accurately during large-scale requests.
- Email notification content has been improved for clarity, even with many files/recipients. Summary information for external sharing files and recipients is now provided, along with a web link to view the full list.
- Increased Convenience with New Core Features:
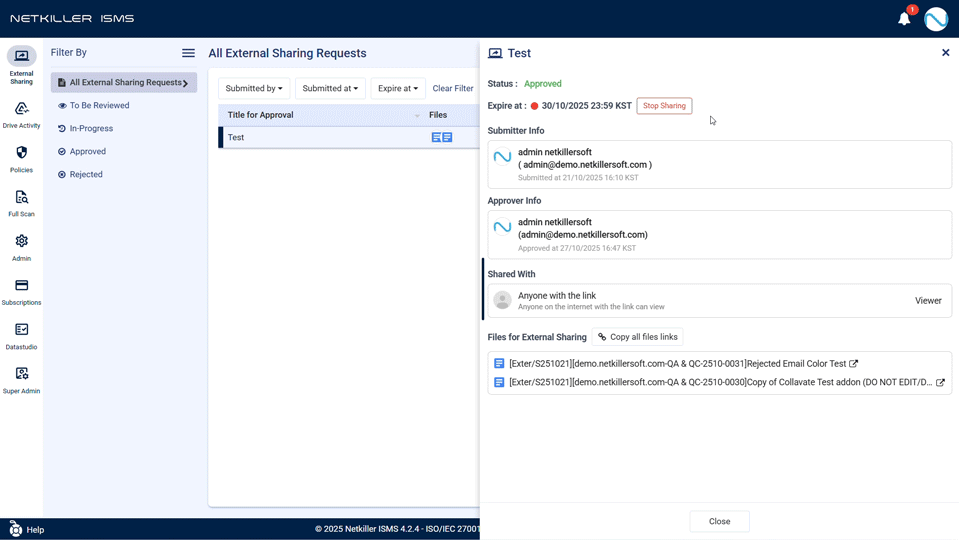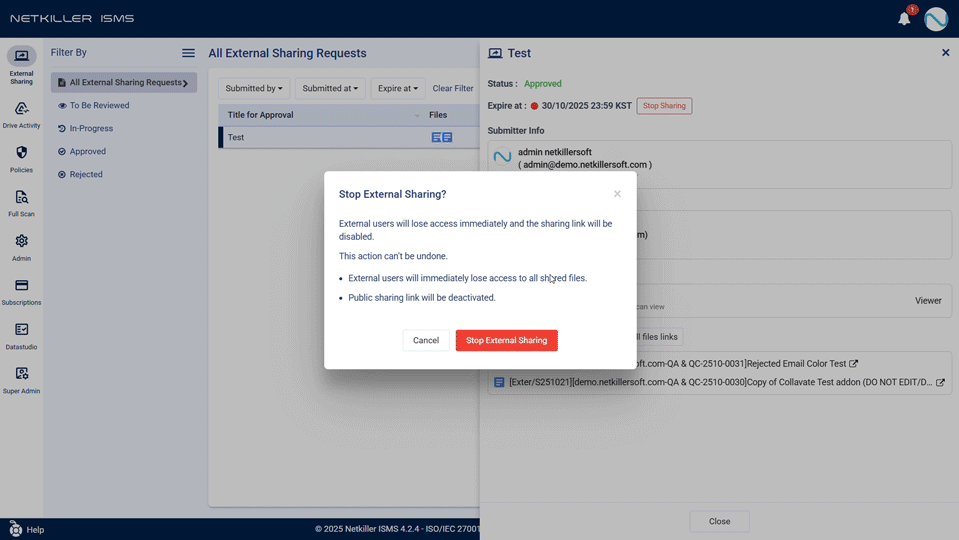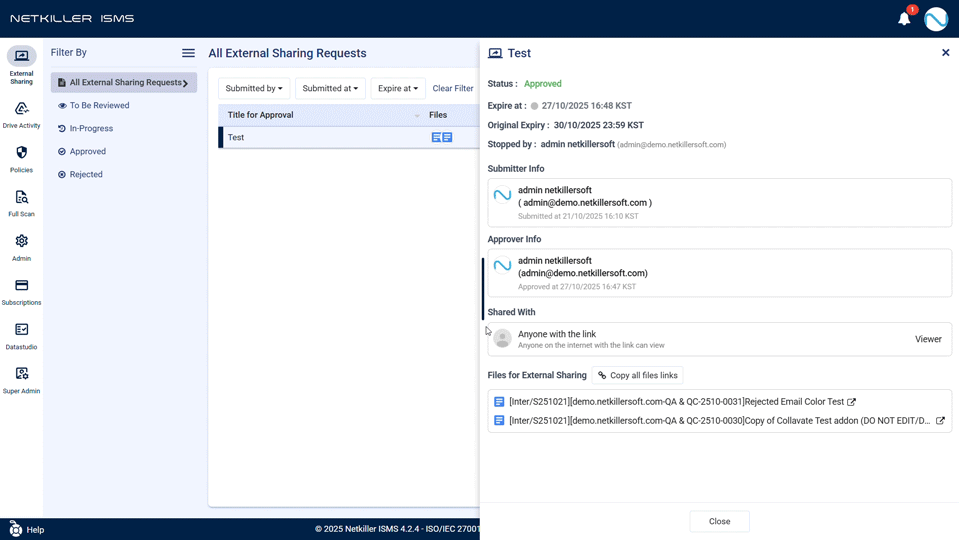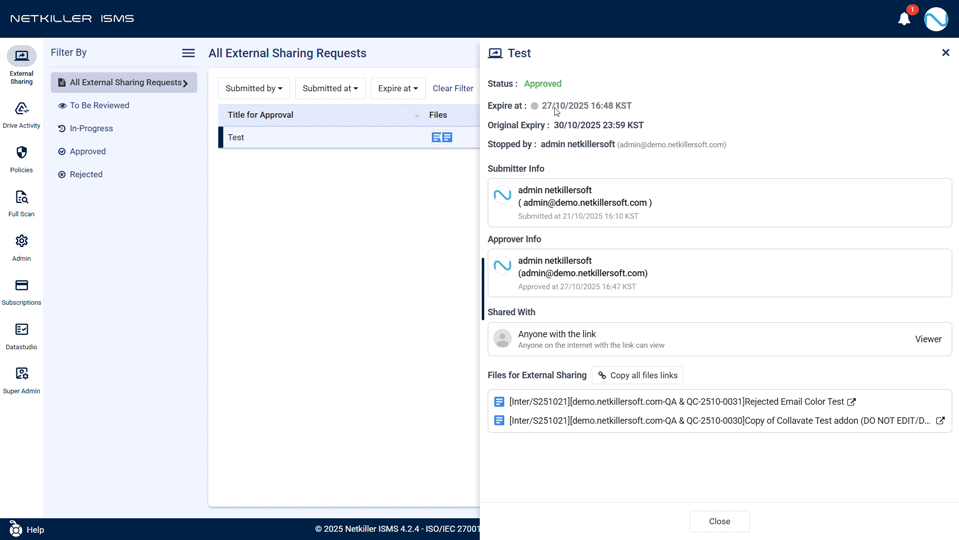
- ‘Immediate Expiry’ for Approved External Shares: When external sharing is no longer needed, a new control feature allows administrators or requesters to immediately stop the share, enabling proactive management of information leakage risks.
- Customizable Org/User Auto-Sync Time: Administrators can now directly set the time for automatic synchronization of organization and user information according to their work hours, supporting immediate system access for new hires, etc.
- Policy-Detected File Report: A dedicated report page has been added to check the list of files detected by policies in one place and filter them by various criteria, making policy violation status management easier. (Initially applied for Remember customer)
- Automated Initial Settings for New Users: Language, time zone, etc., are automatically set for new users upon their first login, reducing the hassle of initial setup and allowing them to start using the system immediately.
- Improved System Efficiency and Accuracy:
- Optimized Weekly Report PDF File Size: The PDF generation method has been improved to drastically reduce the size of weekly report files, allowing users to check and store reports without email capacity concerns.
- Improved GWS Drive Log Sync Speed: Intermittent synchronization delays that occurred during temporary spikes in Google Workspace Drive log traffic have been addressed, allowing users to check the latest activity history more quickly and reliably.
- Optimized Internal System Resource Utilization: System load has been reduced and overall response speed improved by eliminating unnecessary internal API calls.
- Enhanced Database Performance and Stability: Data processing speed for major functions has been increased, and the database connection management method has been optimized for stable service operation.
- Strengthened Background Automation Stability: Issues where background tasks like automatic notifications were delayed under certain conditions have been improved, ensuring stable execution of automated processing functions.
🎨 User Interface (UI) Improvements
Reflecting user feedback, we’ve improved the screen configuration for greater convenience and intuitiveness. Various elements, including file browsing, screen operation, and guidance text, have been refined for enhanced usability and completeness.
- Revolutionized External Sharing Request Experience:
- Convenient File Browsing like Google Drive: The file selection method for external sharing has been renewed with a Drive-like explorer UI. Users can browse the folder structure, find files, and use search/sort functions to quickly select desired files.
- Resizable Side Panel: The width of the panel for external sharing requests/confirmations can be freely adjusted by the user, and the setting is saved for future use. Long filenames can be viewed at a glance.
- Submit External Sharing Approval Request Easily with ‘Link Sharing Only’: The usage method has become more flexible, as external sharing requests can now be submitted by selecting only the ‘Allow link sharing’ option without entering recipient emails.
- Enhanced Input Stability and Convenience: A real-time character count (max 255 characters) is displayed when entering messages or titles, making it easy to check the input range. Stability has been strengthened to prevent the screen from breaking or freezing even when entering long phrases.
- More Natural Korean Expressions: Korean expressions related to permission settings on the external sharing request screen have been refined for better readability.
- Improved Approver Addition Convenience: If an approver is already registered, they can now be added immediately just by entering their email, without needing the dropdown.
- Improved Shared Recipient List Check: Tooltip display has been enhanced so the full list of names can be checked at a glance, even with many shared recipients.
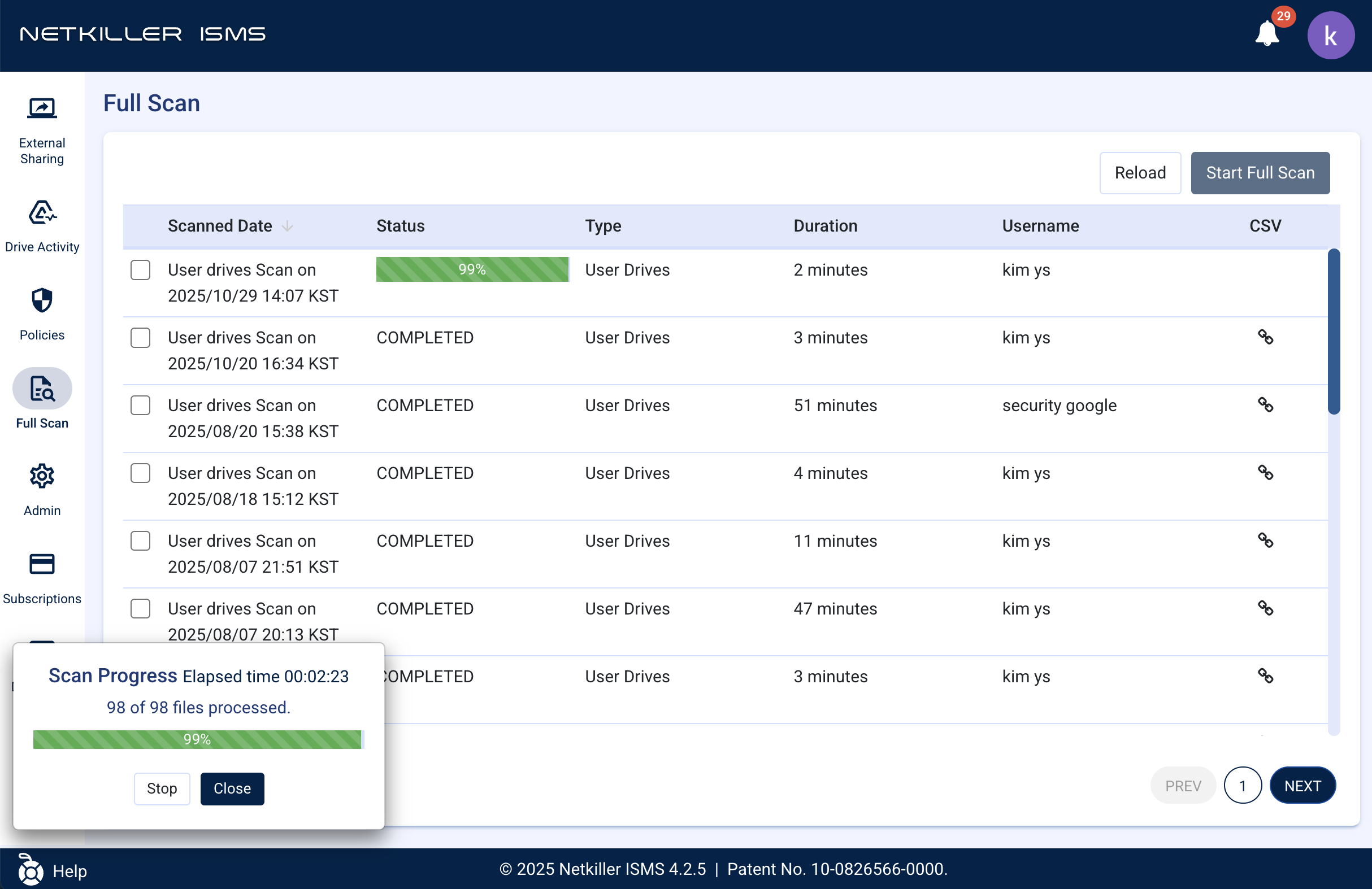
- Improved ‘Full Scan’ Feature Usability:
- Clearer Progress Status: The guidance messages and progress display method shown when running a ‘Full Scan’ have been improved, allowing users to grasp the work status more clearly and intuitively.
- Enhanced Korean Guidance Display Quality: Issues where Korean guidance text was cut off in the ‘Start Full Scan’ modal have been resolved, ensuring all text displays normally.
- Improved Tooltip Display: Visual priority has been adjusted so that guidance tooltips are not hidden behind buttons.
- Overall UI Consistency and Convenience Enhancements:
- Unified Page Navigation Buttons: The design and position of page navigation buttons at the bottom of all list screens have been standardized for consistency.
- Added Sorting for ‘Policy’ List: Management efficiency has been increased by adding the ability to conveniently sort the ‘Policy’ list based on activation status (ON/OFF).
- Improved Guide for First-Time Users: The position of the guide popup displayed upon first login has been adjusted so it doesn’t obstruct menus.
- Enhanced Screen Transition Quality: The UI flickering phenomenon that occurred when navigating to certain screens has been eliminated, providing a more visually stable experience.
- Updated Login Page Information: Information in the footer at the bottom of the login page has been updated to the latest status.
- Clear Logo Display: The issue where the background appeared black when uploading a transparent background logo in company information settings has been fixed, ensuring the logo displays clearly as intended.
- Improved Text Display Accuracy: Issues where some guidance text was cut off or omitted have been corrected.
🔧 Stability and Reliability Enhancements
Overall system stability and data accuracy have been strengthened to provide a reliable service environment at all times.
- Improved Data Accuracy and Management Efficiency:
- Enhanced Organization Info Sync Accuracy: Improvements prevent duplicate organization information from being generated, ensuring the system always maintains the latest accurate status.
- Improved File Activity Log Accuracy: The system has been improved to accurately record file activity status during specific policy executions, preventing confusion during audit tracking and status checks.
- Improved ‘Full Scan’ Time Display: The display of scan progress time has been improved to match the actual work, increasing management efficiency.
- Enhanced External Sharing Function Stability and Convenience:
- Stability Assured with Auto-Recovery of Request Folder: Stability has been enhanced by ensuring the system automatically recovers the internal folder used for external sharing requests if it’s accidentally deleted, allowing the request process to continue smoothly without interruption.
- Ability to Check Request History: The issue preventing navigation to the next page when the external sharing request list was long has been resolved, allowing users to check all request details without omission.
- Consistent and Stable User Experience:
- User Status Changes Reflected Immediately: Login sessions for deactivated users are now terminated immediately, enhancing the accuracy of account management.
- Improved UI Operation Stability: The system now operates smoothly without freezing in various situations, such as dealing with popup windows or long text input.
- Strengthened Input Validation: Areas where unintended input values were allowed, such as adding non-existent users during ‘Full Scan’, have been improved, enhancing data processing accuracy.
- Improved UI Display Quality: UI display errors, such as popup scrolling being unavailable under certain conditions or header logo images appearing broken, have been corrected.
- Stabilized Backend Logic: Backend logic stability has been strengthened for processes like specific date selections or email dispatching.
Netkiller ISMS 4.2.5 has evolved into a more powerful and reliable information security solution based on valuable customer feedback. We will continue to strive to provide the best value through ongoing improvements.
Thank you very much.