Protect Your Google Drive
From

Gemini can access and use your Drive data to train models and power AI features.
Even internal or external file sharing can expose sensitive data without you realizing it.
Netkiller ISMS keeps your organization’s data private and compliant —
by monitoring Drive activity, managing external sharing, and blocking risky exposure.
Secure your Google Drive today
Install from Google Workspace Marketplace, free for 7 days
Trusted globally by organizations





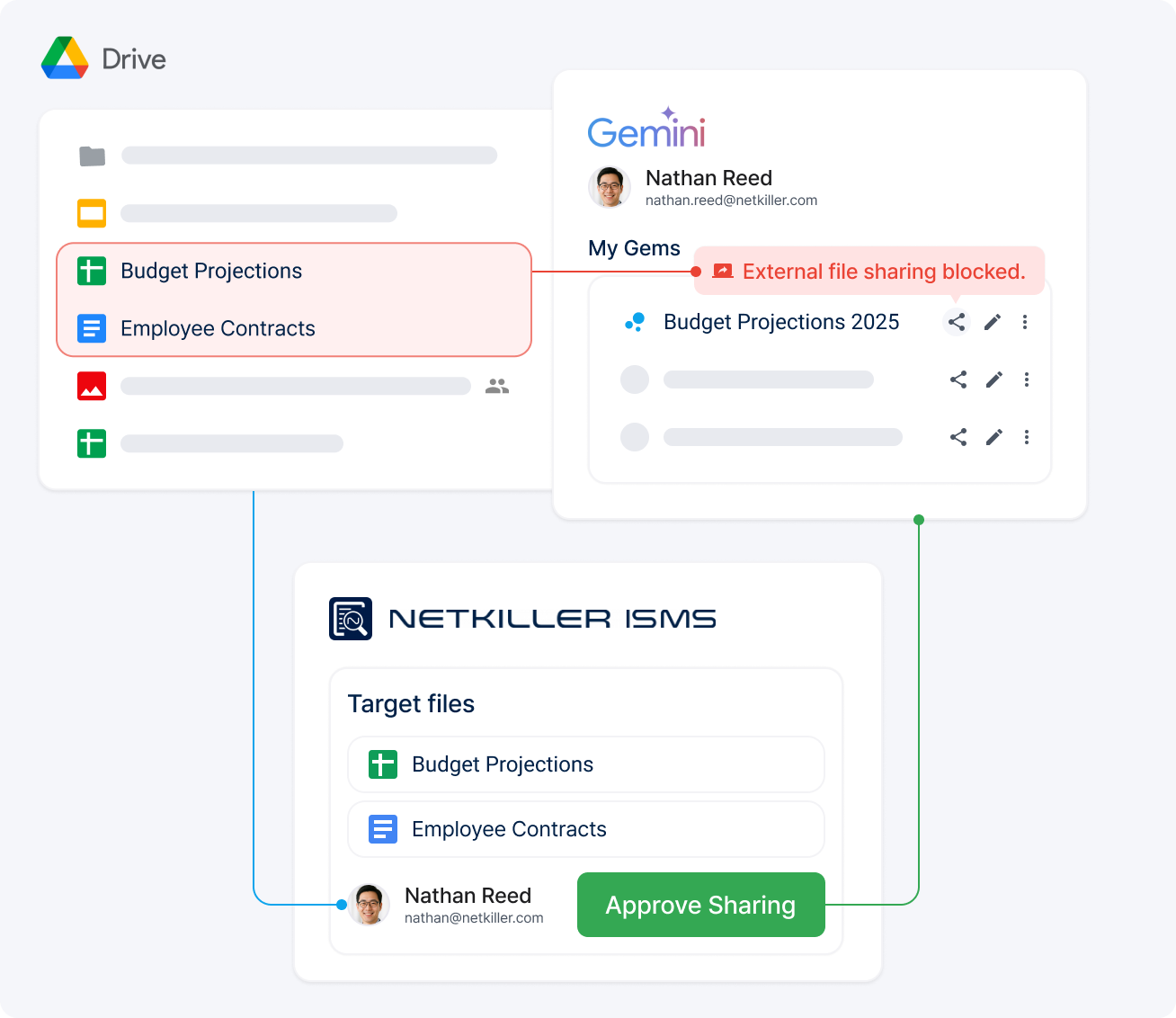
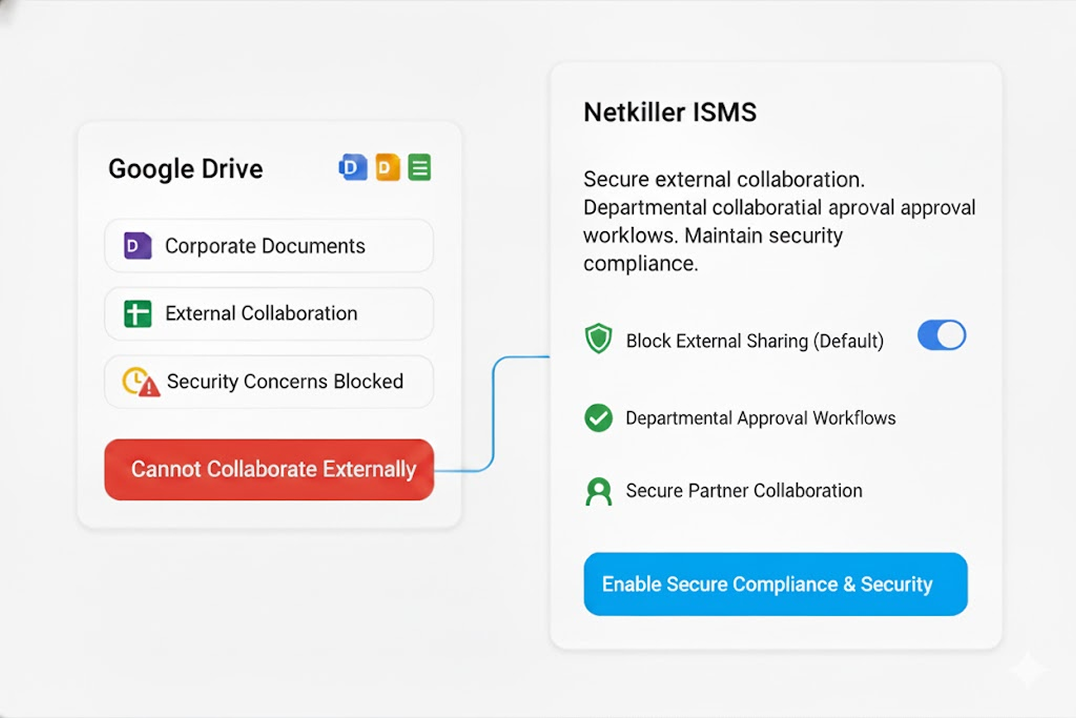
No sharing without approval — not even AI.
Unapproved Drive files and AI ‘knowledge files’ are blocked immediately, while approved shares are safely managed with set durations and permissions, leaving no uncontrolled links behind.
Eliminating Google Drive’s Riskiest
“Security Blind Spots”
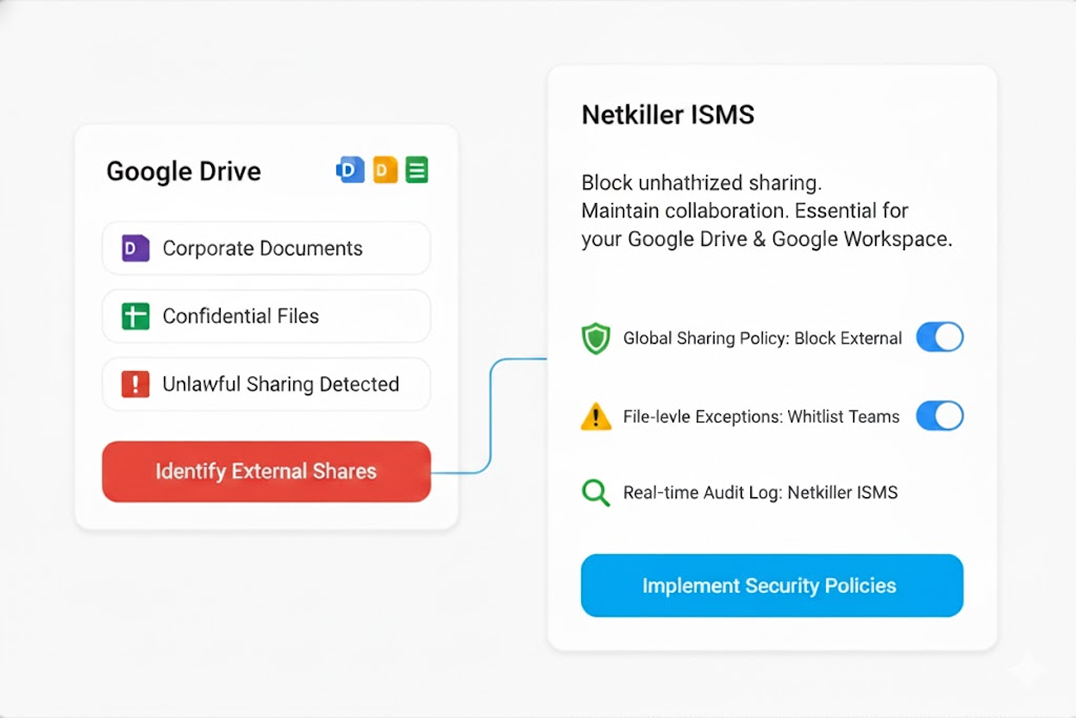
External Sharing
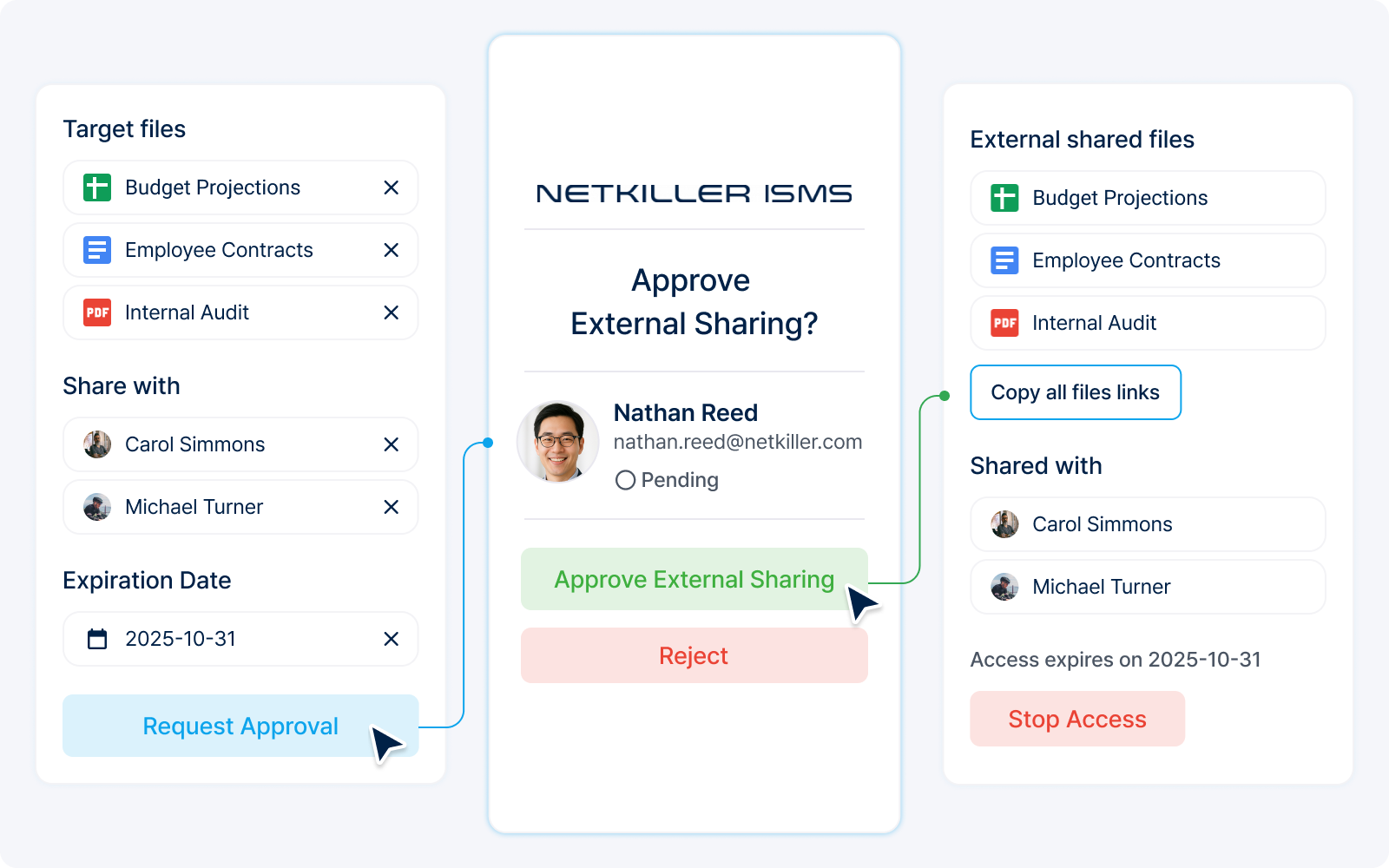
Secure external sharing with approval and automatic expiration to block data leaks at the source.
Drive Activity
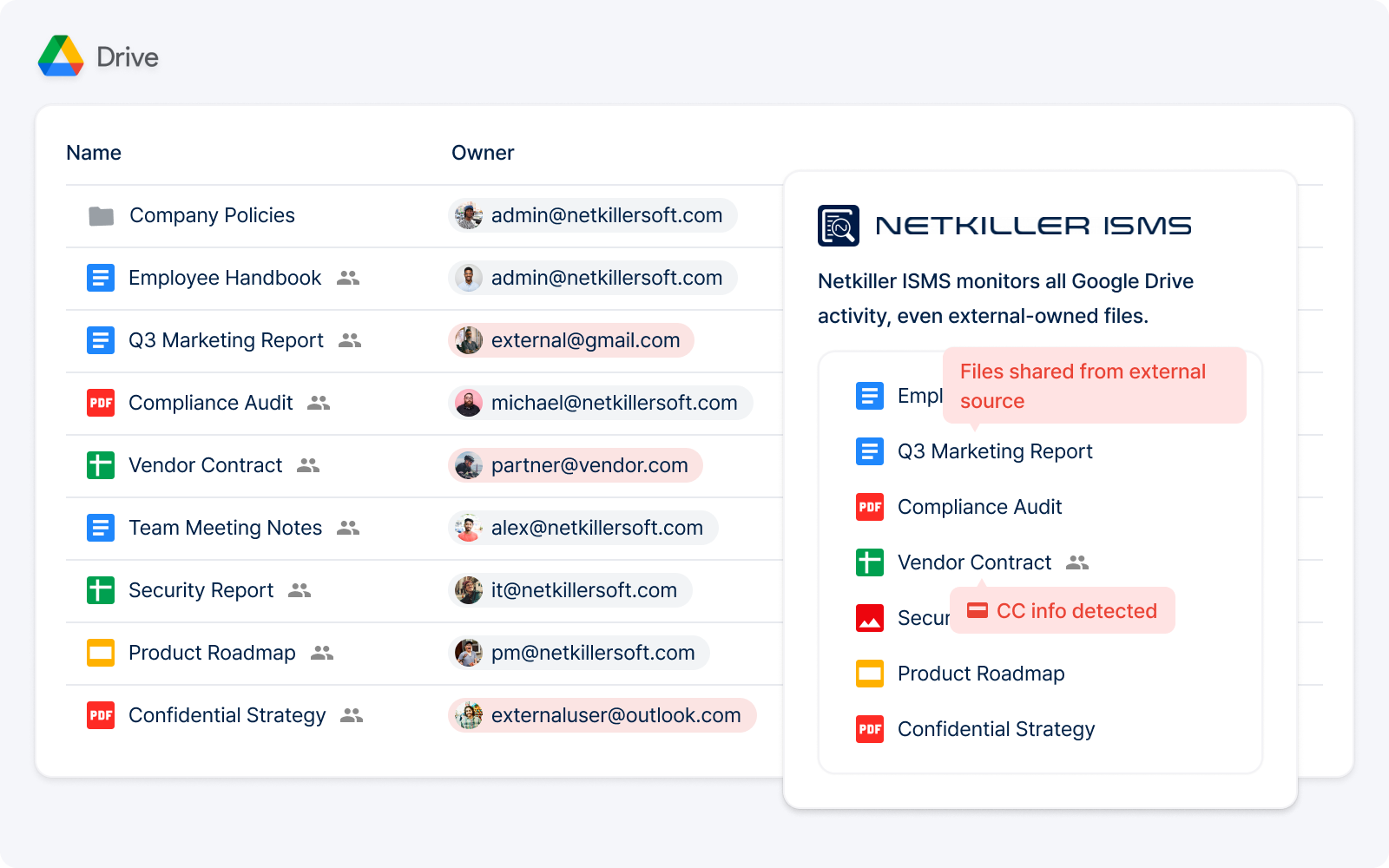
Track every activity — including previously hidden files shared from external sources — without missing a thing.
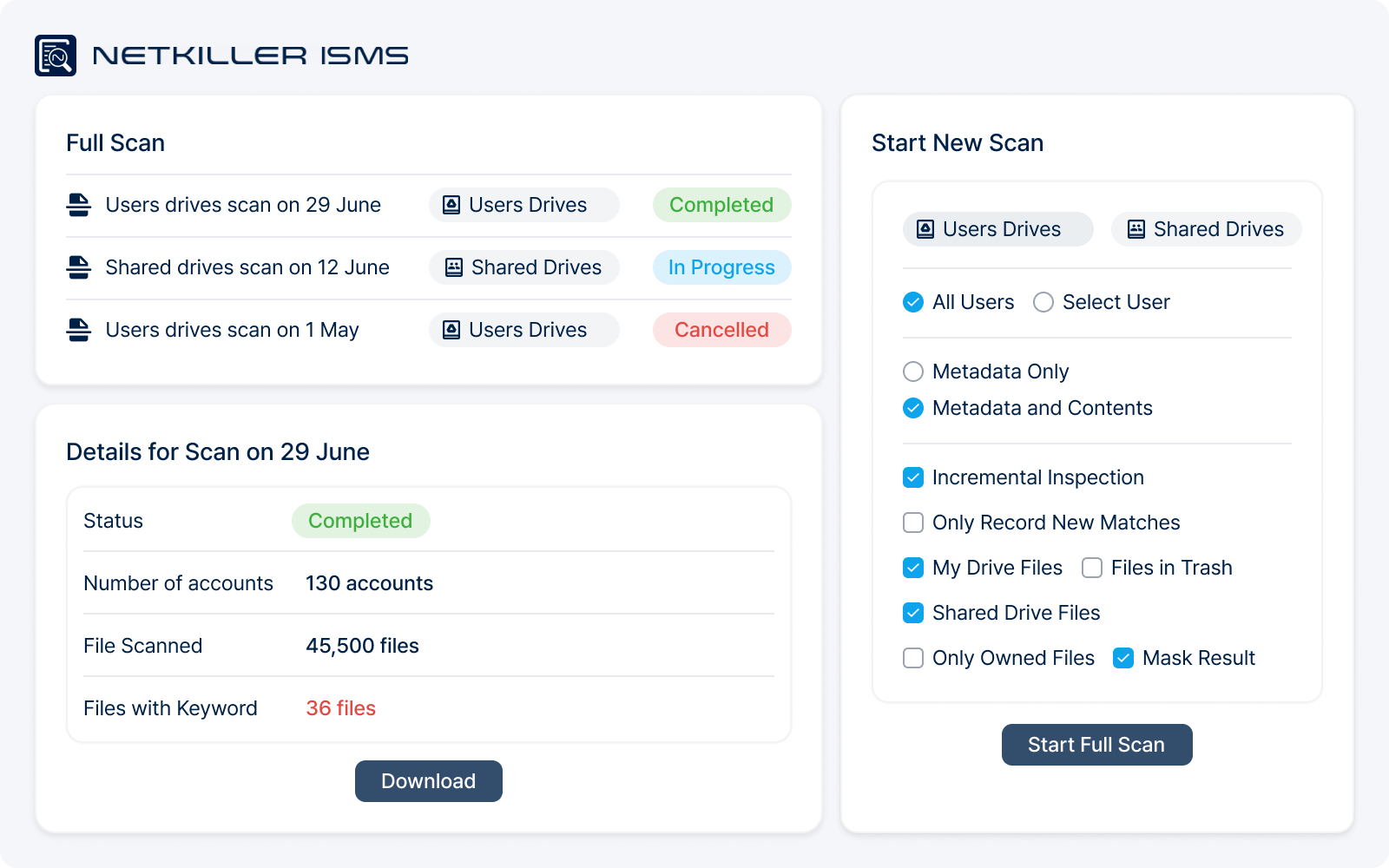
Full Scan
Get a complete snapshot of all dormant external links, sensitive files, and shared files — with a single click.
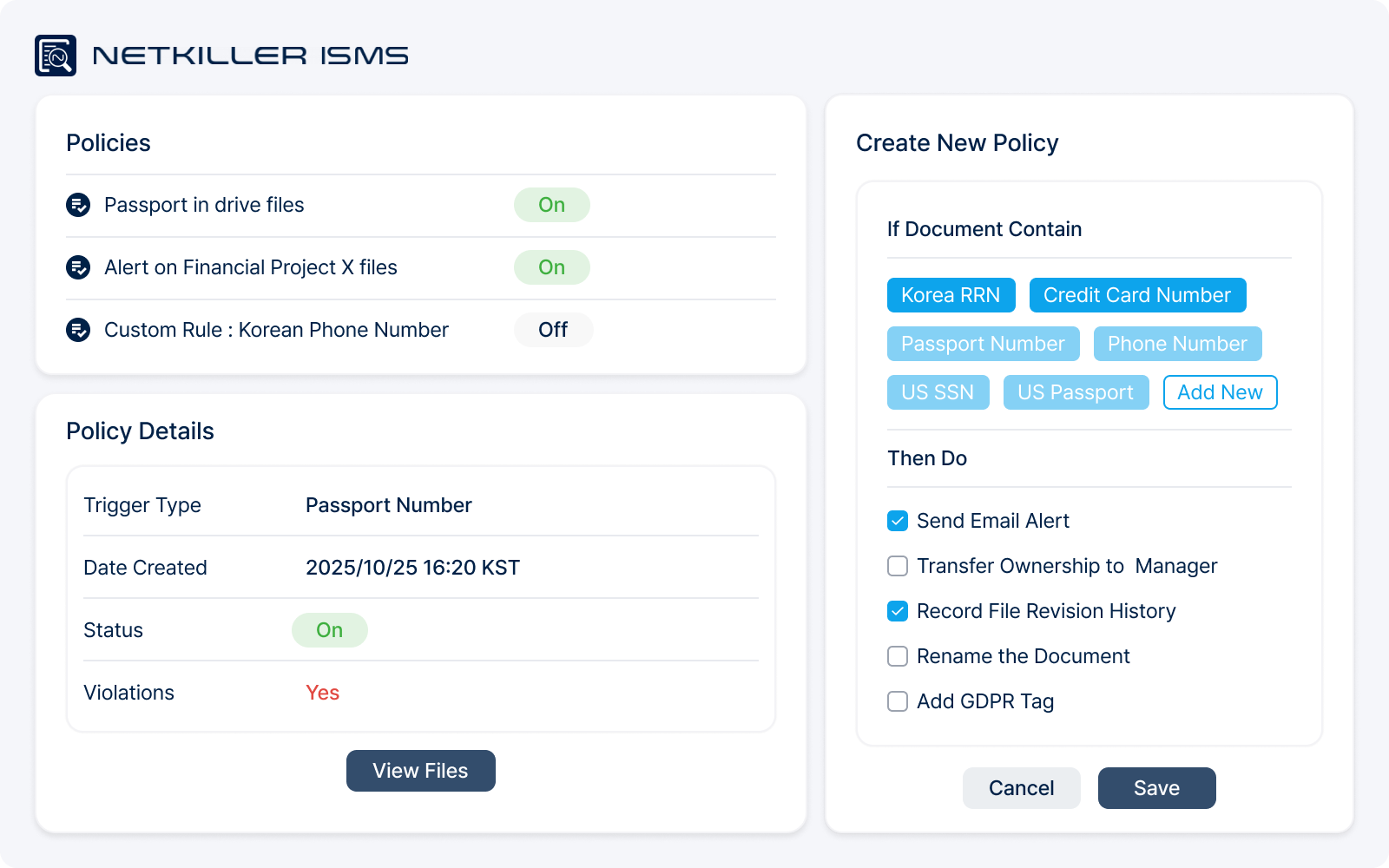
Policies
Control AI leaks and security blind spots with automated policies across all internal and external files — managing both overall file status and real-time activity.
Customizable Platform
Netkiller ISMS 3-Stage Complete Security Framework
Blocking hidden leak activities in externally received files — in real time.
Perfectly control editor resharing, permanent links, and share duration in external sharing.
Perfectly manage abandoned files and all current hidden threats.
Customer Success Story
As the first internet bank not only in our country but also in Asia, we aimed to create an efficient collaboration environment using Google Drive.
However, due to the nature of the financial industry, implementing Google Drive required internal data audits. Additionally, to ensure compliance among employees, regular security audits and reporting were necessary. Security concerns related to externally shared files were also a significant challenge.
After adopting Netkiller ISMS, we were able to effectively meet the requirements for ISMS data security compliance in Google Drive.
Chief Security Officer
The Largest Internet Bank in Korea and Asia
Netkiller ISMS’s 6 Core Capabilities
Real-time Blocking of Hidden Leaks from External File Pasting
In addition to monitoring internal files, we detect and block all risky activities — such as pasting or editing — even within externally received files. This eliminates a major limitation of traditional DLP solutions.
Stop Google’s Security Loopholes: Resharing & Non-Expiring Links
We enforce approval when sharing with non-permitted domains. Link auto-expiration, resharing, and download restrictions are also automatically enforced — closing Google’s native security gaps completely.
Full Scan for Legacy Data and Hidden Threats
Identify and manage sensitive information across all files — including externally received ones — along with risky sharing statuses such as abandoned permissions, public links, and personal Gmail shares, all in one view.
24/7 Automated Defense to Reduce Administrator Workload
Automatically block or quarantine threats the moment they’re detected to secure the critical response window. Apply a unified policy to all internal and external files, significantly reducing manual administrative effort.
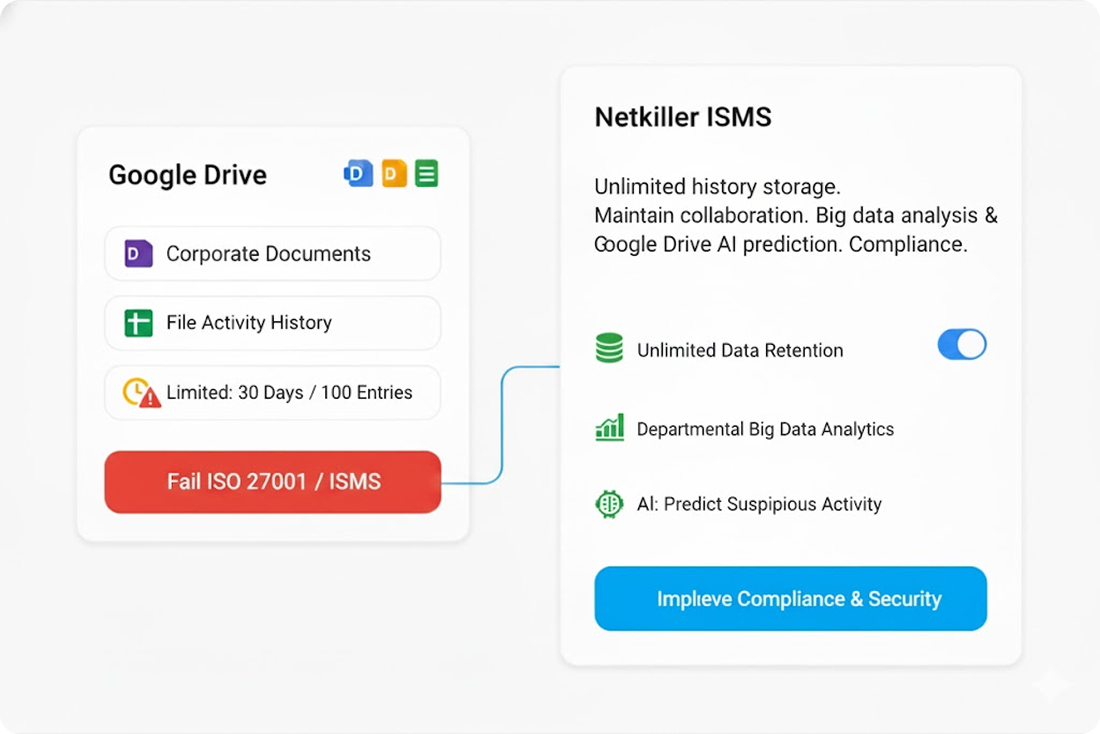
Unlimited Logs for ISMS-Compliant Audit Trails
Overcome Google’s six-month retention limit. We store all activity logs and file revision histories indefinitely, ensuring complete audit trail data for strict compliance standards like ISMS.
Safe Adoption with Sandbox and Flexible Deployment
Safely test in a sandbox environment with no impact on production. Choose the optimal deployment model for your needs — On-Premise, Private Cloud, or SaaS.
Meet the Netkiller ISMS Leadership Team

Charles Lim
Project Manager
Experienced in infrastructure virtualization and hybrid cloud products for enterprise and public sector organizations.

Liam Kim
Head of Solutions

Yeosub Lee
Head of Development
Pricing Plan
For enterprises, a perpetual license is recommended, ensuring security compliance and asset ownership. In contrast, the SaaS subscription service operates on an annual per-user contract, allowing for quick and cost-effective implementation with low initial investment.
Free
Online SaaS Subscription
$0
Per user/year
- Up to 200 users
- Low annual cost
- No server setup required
- Fast deployment
Business
Online SaaS Subscription
$120
Per user/year
- Up to 200 users
- Low annual cost
- No server setup required
- Fast deployment
Enterprise
Perpetual License Software
$600
Per user (one-time purchase)
- 200+ users
- One-time license — no renewal
- On-premise or cloud install
- Full integration & customization

