Netkiller, Google Workspace Managed Security Service
For the past 16 years, Netkiller has accumulated experience and know-how managing the Google Workspaces of over 3000 companies and evolved its Managed Security Service Program (MSSP).
Use Netkiller MSSP with Gemini AI to protect your Google Workspace and experience the power of incident detection and prevention and automated response.
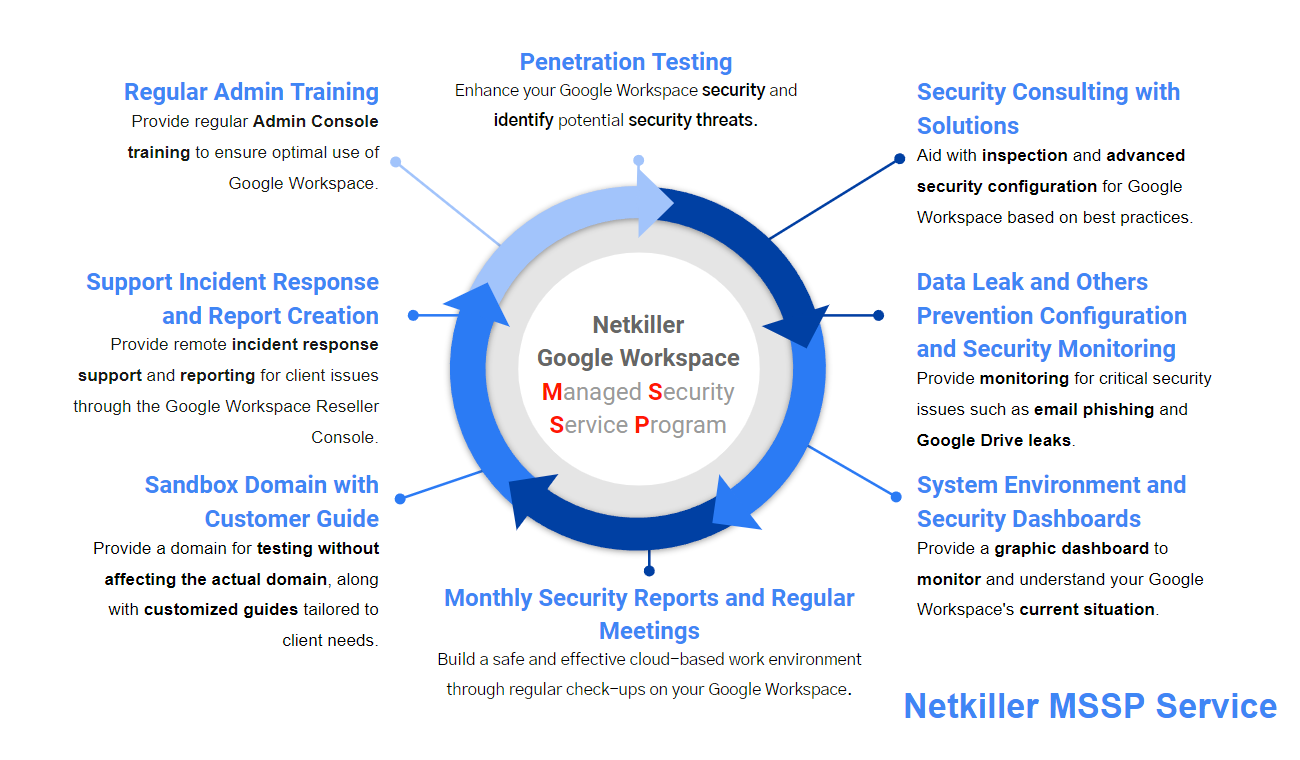
Structure of Netkiller’s Google Workspace Managed Security Service
Netkiller is the first Google Workspace partner in Korea and Asia, and it has developed various features and services for the security of Google Workspace for the past 16 years.
Security Solutions and Consulting Services
Aid with inspection and advanced security configuration for your Google Workspace based on best practices.
Advanced Configurations for Security Incident Prevention
Provide monitoring for critical security issues such as email phishing and Google Drive leaks.
System Status and Security Dashboards
Provide a graphic dashboard to monitor and understand your Google Workspace's current situation.
Monthly Security Reports and Regular Meetings
Build a safe and effective cloud-based work environment through regular check-ups on your Google Workspace.
Sandbox Domain and Custom Services
Provide a domain for testing without affecting the actual domain, along with customized guides tailored to client needs.
Emergency Response Services for Incidents
Provide emergency incident response and detailed after-reports including root-cause analysis and future preventive measures.
Regular Google Workspace Admin Management and Security Training
Provide regular Admin Console training to ensure optimal use of Google Workspace.
Custom Services for your Security Needs
Utilize Google Workspace logs for detailed monitoring to identify security threats, and enhance security by controlling users and Google services through APIs upon specific event detection.
Penetration Testing
Enhance your Google Workspace security and identify potential security threats.

Woori America Bank

Hiossen

Kakao Group
Frequently Asked Questions (FAQ)
In the event of a security incident, the scope of responsibility can vary depending on the nature and cause of the incident. Netkiller MSSP plays the following roles in relation to Google Workspace security management:
- Preventive Measures: Netkiller takes steps to prevent security incidents by providing regular security checks of the client’s Google Workspace environment, early warnings about security threats, and training on optimal security practices.
- Incident Response: In the event of an incident, Netkiller immediately takes action through its incident response team, analyzes the cause of the incident, and develops measures to prevent recurrence. During this process, Netkiller performs roles such as incident investigation, support for data recovery, and provision of related reports.
- Root-Cause Analysis and Future Preventive Measures: Conduct thorough analysis of the incident’s cause and develop strategies to prevent its recurrence.
- Customer Responsibility: Customers are responsible for their own user management, access control settings, and the implementation of security recommendations provided by Netkiller. Additionally, customers must actively cooperate for the early detection and reporting of security incidents.
Ultimately, the responsibility for a security incident is determined based on the cause of the incident and the actions taken at the time of its occurrence. Netkiller is committed to working with customers to prevent security incidents and, should they occur, to respond effectively. The key is to minimize the risk of security incidents and respond quickly and effectively when they occur through continuous communication and cooperation between Netkiller and its customers.
Netkiller prioritizes the protection of customer data and personal information security above all else. To this end, we have implemented a strict information security management system and protect our customers’ sensitive information and secrets in the following ways:
- International Standards Compliance: All our business processes adhere to the ISO 27001 Information Security Management Standard, for which we regularly undergo audits. This ensures that our information security management system meets the highest internationally recognized standards.
- Strong Authentication Methods: We apply two-factor authentication (2FA) for all Google Workspace and Google Drive accounts. Notably, we use Google’s own 2FA method and FIDO Key hardware security keys instead of mobile text authentication to prevent phishing attacks.
- Device Security: We prohibit the use of Windows PCs for employees involved with Netkiller MSSP and only allow devices operating on Chrome OS and Apple Mac OS with Google Workspace MDM installed. All data drives are encrypted, and for mobile devices, only verified Samsung Android or Apple iPhone are used.
- Remote Meeting Security: We provide an end-to-end encrypted meeting environment using Google Meet for Enterprise and utilize encrypted landline communication services through RingCentral Voice IP Phones.
- Real-time Security Auditing and Blocking: We prevent the transmission of sensitive personal and security password information through Google Workspace and use Netkiller ISMS products to audit and block security information for all Google Drive document activities in real-time.
- Continuous Security Education and Inspection: We regularly conduct security training for employees and perform periodic security checks on devices and operating systems.
Netkiller protects customers’ sensitive information and secrets at the highest level through these thorough data protection protocols, prioritizing customer trust to the utmost.
For more details, see “Netkiller Customer Data Protection Protocols.
Netkiller has established systematic procedures to respond to information security incidents that may occur within the Google Workspace environment. These procedures are based on the ISO 27001 standard and include stages of incident identification, reporting, investigation, response, and recovery. Below are the key stages of Netkiller’s incident response process:
- Incident Identification: This stage involves detecting and documenting a security incident. All security incidents must be appropriately classified and reported to the incident response team.
- Incident Discovery: This stage involves recognizing that a security incident has occurred and being the first to respond, including the process of discovering and documenting the incident.
- Incident Detection: Identify the type, scope, and impact of the incident to classify its significance. This is a crucial step for an appropriate response.
- Initial Response: The first action taken in response to an incident, including measures to prevent immediate further damage. This may involve isolating systems and preserving evidence if necessary.
- Incident Investigation: This stage involves investigating the cause of the incident and understanding how it occurred, including data recovery, vulnerability analysis, and assessment of potential additional damages.
- Incident Response: This stage involves implementing actions to address identified vulnerabilities and recover from damages caused by the incident, which may include establishing and executing long-term recovery strategies.
- Recovery Actions: Carry out tasks to return to normal operational status, which may include restoring systems and data, as well as resuming services.
- Issue Resolution and Report Writing: Conclude all investigation and response activities related to the incident and compile an incident report. This report includes details of the incident, causes, responses, recovery activities, and information on future preventive measures.
- Plan and Implement Recurrence Prevention Measures: Based on lessons learned from the incident, plan and implement measures to prevent the incident from recurring. This may include improvements to policies and procedures as well as enhancing security awareness training.
Netkiller effectively addresses potential incidents within the customer’s Google Workspace environment through these systematic incident response procedures, thoroughly protecting the customer’s information security.
The ultimate responsibility typically falls on the company’s CEO or managing director, who bears overall accountability for the company and is ultimately responsible for major issues such as security incidents. However, this can vary depending on specific circumstances and the company’s internal organizational structure and responsibility sharing approach, which may designate a different person to bear the ultimate responsibility.
In the event of a security incident, such as the leakage of customer personal information, responsibility can lie with various parties, and legal issues can become complex. The primary entities to consider for responsibility are as follows:
- Personal Information Management Officer: Responsible for personal information processing in accordance with local regulations, and accountable for any shortcomings of security measures.
- Service Provider: If responsible for processing personal information, they are liable in accordance with relevant laws and contractual terms.
- System Developer: If they developed the system that stores personal information, they are responsible for incidents resulting from vulnerabilities in the system.
- Internal Employee: The employee is responsible for incidents caused by their intentional actions or negligence, as legally determined.
- Others: If external attackers or other parties are involved, their responsibility is also considered, and joint or several liabilities may arise.
- Reference material: Determining the responsibility is a complex process that may require the assistance of legal professionals. If a personal information leakage incident occurs, it is crucial to promptly consult with legal experts to clarify the responsibilities and take measures for damage recovery.
Customer personal information can include a variety of information, and the specific details may vary depending on the industry, type of service, and purpose of personal information processing. However, the following types of information are commonly included:
1) Basic Personal Information:
- Names: First and Last name(s)
- Birth date: Birth date, age
- Sex: Male/Female
- Address: Address, ZIP Code
- Phone number: Cellphone number, landline
- Email: Email Address
- IP Address: IP Address for connecting to and using the internet
2) Physical Information:
- ID Information: State/Federal ID number, Driver’s License ID number, Passport number, etc.
- Physical Characteristics: Height, weight, skin color, hair color, eye color, etc.
- Health Information: Medical history, current medications, allergy information, etc.
3) Financial Information:
- Bank account number: Account number, Accountholder name, Bank Code, etc.
- Credit Card Information: Credit Card number, Expiration Date, Security Code (CVV/CVC), etc.
- Income Information: Salary, Assets Information, etc.
4) Online Activities Information:
- Usage History: Websites you visited, search history, purchase history, etc.
- Cookies: Data automatically saved when you visit a website
- Social Network Information: Social Network profile information, posts, “likes,” follow information, etc.
5) Other Information:
- Hobbies and Interests: Favorite foods, movies, music, etc.
- Family Information: Information on family members, contact details, etc.
- Workplace Information: Name of the workplace, position, contact details, etc.
Bank account and card information are classified as sensitive information under personal information protection laws, requiring even more stringent protection. Therefore, entities cannot collect or use bank account or card information without the customer’s consent. When such information is collected, a clear and specific purpose must be presented, and appropriate security measures must be put in place for safekeeping and management.
Phone Number
Phone: 646-758-0100 (NY), 408-560-0556 (CA)
KST Timezone Phone: +82-2-2052-0453 (Seoul, Busan)
24-hour Customer Service Availability (guaranteed response within 20 minutes)
In case of an emergency issue, please send an email to support@netkiller.com with the word “URGENT” added to the subject line. For issues determined to be emergency failures, Netkiller Global Support Team provides technical support 24 hours a day, 365 days a year based on Netkiller Service Level Agreement (SLA).